Microsoft has recently introduced Azure Service Groups (public preview since August 2025) – a feature designed to bring flexibility and clarity into how you organize and monitor your Azure environment.
While Resource Groups and Management Groups remain essential governance constructs, Service Groups add a new layer: a logical overlay across subscriptions and resources, without interfering with security or policies.
View more on: https://learn.microsoft.com/en-us/azure/governance/service-groups/overview
Contents
🔍 What Is a Service Group?
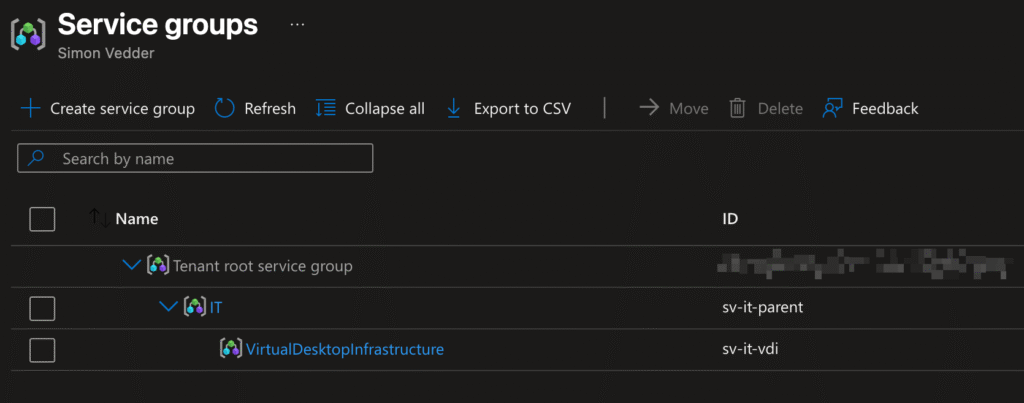
A Service Group (SG) is a tenant-level container that can include:
- Subscriptions
- Resource Groups
- Individual resources
Unlike Resource Groups, Service Groups are:
- Optional – resources can exist without them
- Non-intrusive – they don’t change access or lifecycle
- Flexible – resources can belong to multiple SGs
👉 Think of them as a lens you can put over your cloud estate to view applications, services, or departments holistically – no matter where the underlying resources live.
📚 Key Information
- Cross-subscription grouping – Group anything across your tenant.
- Nested hierarchies – Up to 10 levels deep.
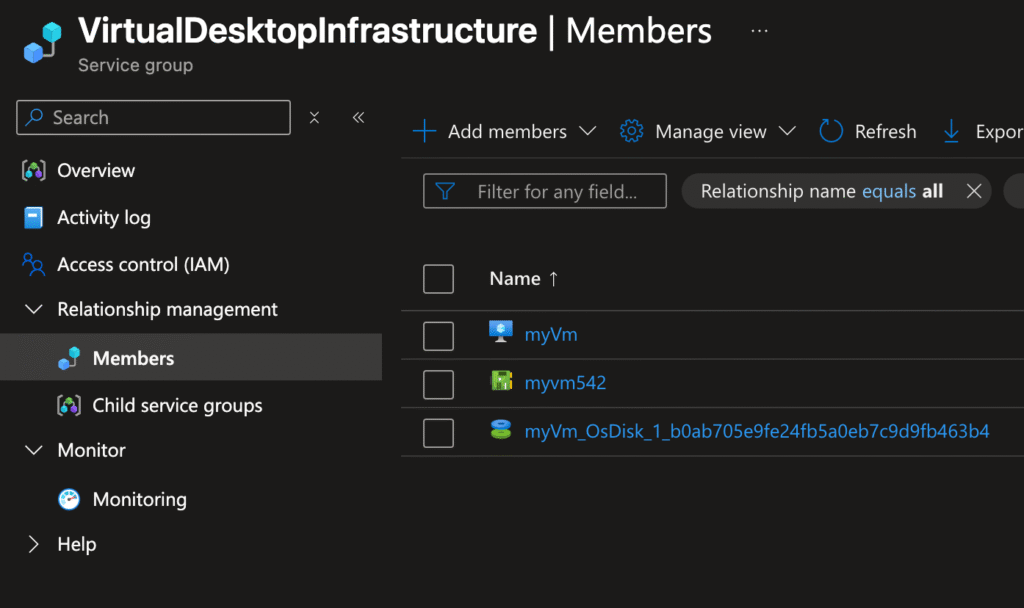
- Multiple memberships – A VM could belong to an “App Service Group” and a “Cost Center Service Group” at the same time.
- Monitoring support – Works with Azure Monitor, allowing application-centric dashboards.
- Root Service Group – Created automatically at the tenant level, cannot be changed or removed.
- Security boundary intact – Service Groups never override RBAC or policies.
💡 Use Cases
- 🏥 Application health monitoring Group all resources powering a business app across subscriptions into one Service Group for unified health checks.
- 📈 Cross-subscription reporting Aggregate performance metrics without restructuring.
- 👥 Persona-based views Create different overlays: by department, environment (Dev/Test/Prod), or cost center.
- 🔎 Inventory clarity Easily answer: “Which resources power Service X?”
✅ Pros and ❌ Cons
Pros
- ✅ Cross-subscription grouping
- ✅ Nested hierarchies
- ✅ Multiple group memberships possible
- ✅ No security risks (no implicit access)
- ✅ Application-centric monitoring
Cons
- ❌ No RBAC or policy enforcement
- ❌ Still in public preview
- ❌ Additional construct to manage
- ❌ Some services/tools not yet fully integrated
🔄 Service Groups vs. Resource Groups
| Feature | Resource Group 🗂️ | Service Group 🧩 |
| Scope | Bound to one subscription | Tenant-wide, across subscriptions |
| Purpose | Deployment, lifecycle, access | Logical overlay for monitoring & visibility |
| Security | Supports RBAC & policies | ❌ No RBAC, no policies |
| Nesting | Flat structure only | Up to 10 levels deep |
| Dependency | Mandatory for every resource | Optional, resources can join many |
| Best For | Operational management | Reporting, monitoring, grouping by app/team |
👉 In short:
- Resource Groups = operational unit (where resources live and how they’re managed)
- Service Groups = organizational lens (how you want to see and group resources)
⚙️ Limitations & Naming
- Limits:
- Max 2,000 members per subscription
- Max 10,000 Service Groups per tenant
- Naming:
- Up to 250 characters for IDs/names
- Supports letters, numbers & special symbols
- Root SG: Non-editable, auto-created per tenant
- Preview status: Features may evolve before GA
🔑 Permissions & Roles
Managing Service Groups involves two layers of permissions:
- On the Service Group itself
- Service Group Administrator – full control over SGs and memberships
- Service Group Contributor – manage SG lifecycle, but no role assignments
- Service Group Reader – read-only access
- On the resources you want to add Membership is managed via the resource relationship type Microsoft.Relationships/serviceGroupMember.
- To add or remove a resource, you need write or delete permissions on this relationship at the resource scope (subscription, RG, or resource).
- To view membership, you need read permissions.
👉 This ensures a strong security boundary:
- Having Service Group rights doesn’t give you access to the resource.
- Having resource access doesn’t give you Service Group rights.
- You need both to manage membership safely.
🎯 Why Service Groups Matter
As Azure estates grow, complexity skyrockets:
- Hundreds of subscriptions
- Applications spanning multiple RGs
- Different teams needing different “views”
Service Groups offer exactly that flexibility. They don’t replace Resource Groups or Management Groups – they complement them by giving dynamic, application-centric visibility.
💭 Personal Take
Azure Service Groups feel like the missing puzzle piece in Azure’s governance and monitoring model. They won’t change how resources are deployed or secured, but they’ll make it far easier to understand, monitor, and communicate how your environment is structured from an application or business perspective.
👉 Up until now, many organizations heavily relied on tagging to group resources by department, application, or cost center. While tagging remains useful (especially for automation, billing, and policy enforcement), Service Groups can act as a more powerful extension:
- Unlike tags, they support hierarchies (up to 10 levels).
- They allow cross-subscription views.
- They provide native integration with Azure Monitor.
So while Service Groups may not completely replace tags, they can significantly reduce the complexity of tag-based grouping and deliver a richer, application-centric view.
👉 I expect that once they reach GA, Service Groups will quickly become a standard tool for Cloud Architects and Ops teams to tame complex Azure estates.
